In an era where cyber threats are becoming increasingly sophisticated, traditional security models are proving inadequate. Organizations can no longer rely on the assumption that everything inside their network is secure. This outdated approach has given way to a more robust and comprehensive security strategy known as the Zero-Trust security model. The shift towards Zero-Trust is not just a trend; it’s a necessity in today’s digital landscape. This article delves into the rise of Zero-Trust security models, exploring their significance, core principles, and the impact they have on modern cybersecurity.
Understanding the Zero-Trust Security Model
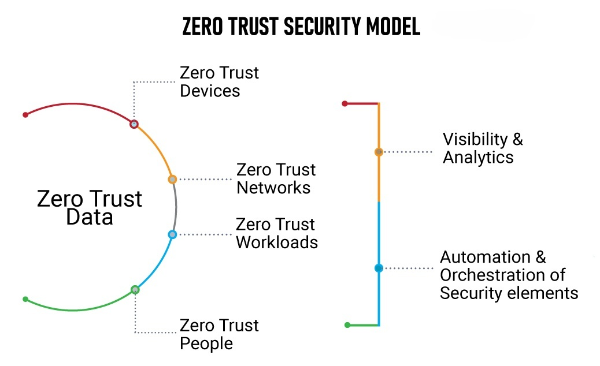
The Zero-Trust security model represents a major shift from the conventional perimeter-based approach. Traditional security models assume that anything inside the network is trustworthy, while threats are considered external. This model worked well when organizations had clear, well-defined perimeters. However, with the rise of cloud computing, remote work, and the Internet of Things (IoT), these perimeters have become increasingly porous, making the traditional approach obsolete.
Zero-Trust, as the name implies, operates on the principle of “never trust, always verify.” It assumes that threats can originate both inside and outside the network. Consequently, no entity, whether a user or a device, is trusted by default. Instead, every access request is treated as if it comes from an open network, requiring strict verification before granting access.
Core Principles of Zero-Trust
Least Privilege Access: One of the foundational principles of Zero-Trust is the concept of least privilege access. Users and devices receive only the minimum level of access necessary to perform their tasks. By actively limiting access, organizations significantly reduce the potential attack surface, which mitigates the risk of lateral movement within the network during a breach.
Microsegmentation: Microsegmentation involves dividing a network into smaller, isolated segments, each protected by its own security controls. This approach ensures that even if an attacker compromises one segment, the breach cannot easily spread to other parts of the network. As a result, microsegmentation plays a critical role in containing threats and minimizing their impact.
Continuous Monitoring and Validation: Zero-Trust demands continuous monitoring of all network activities and assets. This constant vigilance allows for the detection and real-time addressing of any suspicious behavior or anomalies. Unlike traditional security models, which rely on periodic checks, continuous monitoring ensures that organizations are not left vulnerable to attacks occurring between these checks.
Identity Verification and Multi-Factor Authentication (MFA): Zero-Trust focuses on rigorous identity verification. Each user and device must prove their identity before access. Multi-Factor Authentication (MFA) is crucial. It requires multiple forms of verification, like a password and a fingerprint. Implementing MFA adds a vital layer of security.
Data Protection: In a Zero-Trust model, data protection is paramount. Organizations must encrypt data at rest and in transit, enforce strict access controls, and adopt proactive measures to prevent unauthorized access. These enhanced practices are crucial for maintaining security and ensuring data integrity and confidentiality in a Zero-Trust environment.
The Driving Forces Behind Zero-Trust Adoption
The rise of Zero-Trust is driven by several key factors that underscore the need for a more secure and resilient approach to cybersecurity.
Increased Sophistication of Cyber Threats: Cybercriminals now use increasingly sophisticated tactics to breach networks. From advanced persistent threats (APTs) to ransomware and phishing attacks, the threat landscape has become more complex. Zero-Trust offers a proactive defense mechanism that can counter even the most advanced threats by assuming no one can be trusted by default.
The Shift to Remote Work: The global pandemic accelerated the shift to remote work, forcing organizations to rethink their security strategies. With employees accessing corporate networks from various locations and devices, the traditional perimeter-based security model has proven inadequate. Zero-Trust addresses these challenges by verifying every access request, regardless of the user’s location.
Cloud Computing and IoT Proliferation: The widespread adoption of cloud computing and IoT devices has blurred the lines of network perimeters. As data now resides and is accessed across multiple environments, traditional methods of securing it have become ineffective. Zero-Trust solves this problem by treating all environments as untrusted, requiring strict authentication and authorization for every interaction.
Regulatory Compliance: As data privacy regulations tighten, organizations face growing pressure to secure sensitive information. Zero-Trust supports compliance by implementing robust access controls, encryption, and continuous monitoring. This approach not only protects data but also demonstrates a commitment to security, enhancing the organization’s reputation.
Challenges and Considerations: Overcoming Obstacles in the Rise of Zero-Trust Security Models
While Zero-Trust offers a robust framework for enhancing security, organizations must be ready to tackle the challenges that come with implementing and maintaining this model.
Complexity of Implementation: Implementing Zero-Trust, especially in large organizations, can be complex and requires careful planning and coordination across departments.
Without a clear roadmap, the implementation can quickly become overwhelming, leading to security gaps and vulnerabilities within the network.
As organizations embrace the rise of Zero-Trust security models, they must manage every phase meticulously to avoid such pitfalls.
Balancing Security with Usability: Finding the right balance between security and usability is a critical challenge in Zero-Trust security models.
Strict access controls and continuous verification sometimes create friction, potentially impacting user productivity and workflow efficiency.
Organizations must actively ensure that security measures do not interfere with employees’ tasks while still maintaining strong network integrity.
Striking this balance is essential for successfully adopting and implementing the rise of Zero-Trust security models.
Legacy Systems and Integration: Many organizations still rely on legacy systems that may not be compatible with Zero-Trust principles. Integrating these systems into a Zero-Trust framework can be challenging and may require significant upgrades or replacements. Organizations must carefully evaluate their existing infrastructure and determine the best approach to integrating Zero-Trust without disrupting operations.
Cost Considerations: Implementing Zero-Trust can be resource-intensive, requiring investments in new technologies, training, and ongoing maintenance. While the long-term benefits of Zero-Trust far outweigh the costs, organizations must carefully budget for the transition and ensure they have the necessary resources to sustain it.
The Future of Zero-Trust Security
The rise of Zero-Trust security models signals a significant shift in how organizations approach cybersecurity. As cyber threats evolve, the need for a more dynamic and comprehensive security strategy becomes increasingly clear. Zero-Trust provides a robust framework that directly addresses current security challenges while also adapting to future threats.
Looking ahead, Zero-Trust will likely become the standard for cybersecurity across industries. As organizations embrace digital transformation, Zero-Trust principles will play a crucial role in securing data, protecting assets, and maintaining trust in an increasingly interconnected world.
Moreover, the development of artificial intelligence (AI) and machine learning (ML) will further enhance the effectiveness of Zero-Trust models. These technologies enable more advanced threat detection, automate responses to security incidents, and improve user behavior analysis, making Zero-Trust even more resilient against emerging threats.
Conclusion
The rise of Zero-Trust security models represents a fundamental shift in how organizations protect their digital assets. By moving from a perimeter-based approach to one that assumes no trust, organizations can enhance their defenses against the growing complexity of cyber threats. The core principles of Zero-Trust—least privilege access, microsegmentation, continuous monitoring, identity verification, and data protection—offer a comprehensive framework for boosting security.
Although implementing Zero-Trust presents challenges, the benefits far outweigh the costs. Organizations that embrace Zero-Trust will better secure their networks, comply with regulations, and safeguard their reputation. As cyber threats evolve, Zero-Trust will remain a crucial component of modern cybersecurity strategies.
In an era where trust itself poses a vulnerability, Zero-Trust stands as the key to resilience.
